SaaS Infrastructure Details¶
Important
We’ll talk about our own infrastructure security policies in the following sections of this document, however they’re irrelevant if you choose the self-hosted option.
Hosting Policies¶
Scaleway¶
Toucan Toco SaaS applications can be hosted on dedicated servers provided by Scaleway.
The datacenters DC3/DC5 are physically located in Vitry (France) and respects all hosting standards (security, network, client isolation):
- pci-DSS (2017)
- ISO 27001 (2017)
- HDS (2017)
- ISO 50001 (2014)
- Tiers III design by the Uptime Institute (2014)
All the details of the datacenters are described in the Scaleway public documentation:
AWS¶
Since Toucan Toco is present in the US, we are also able to host our customers’ projects on Amazon Web Services.
We mainly use dedicated Amazon Elastic Compute Cloud instances to host all the parts of a project’s stack.
We can deploy in all AWS regions.
All of AWS’s datacenters respect the “Amazon’s Controls” policies and all hosting standards (security, network, client isolation):
All details about the AWS compliance/certifications are fully described and available on the official website.
Azure¶
We are able to host our customers’ projects on Azure.
We can deploy on all Azure areas.
All Azure datacenters respect the Azure compliance policies and all hosting standards:
All details about the Azure compliance certifications are fully described and available on the official website.
OVH¶
We are also able to host our customers’ projects on OVH cloud
Our datacenter is physically located in Gravelines (France) and respects all hosting standards (security, network, client isolation):
All details about the OVH certifications are fully described and available on their official website.
Please note our hosting providers never get access to our servers, logs or your data. They are only an hardware and services supplier, we manage all the VMs or bare-metal servers.
Infrastructure Security Policies¶
DDOS Prevention¶
All our servers come with standard DDOS protection, including automatic mitigation from common attacks with a geographic based database.
All the details of the DDOS protection implementation are described in its official public documentation.
Network Filtering¶
From Internet¶
We respect the usual best practices for SaaS hosting:
- We only expose HTTPS, HTTP (which is automatically redirected to the HTTPS).
- We do not expose management interfaces directly to the Internet. We require a VPN connection first, using a strong 2-factor authentication (certificate and credentials).
Between Instances¶
On our cloud offer, we ensure that the data of each of our clients is completely isolated from any other client’s data. Each client runs different private containers for:
- its application server (API)
- its database (MongoDB)
- its cache (Redis) Containers are operated by Docker, linked using Docker networks and exposed only to other necessary containers (e.g.: Redis container is not linked to MongoDB container).
Thus, only the container API is able to send requests to the associated database container.
We ensure isolation between clients with different Docker networks.
Of course with our dedicated SaaS mode, all of your stack will be isolated by design because you will be given your own dedicated server in the Toucan Toco infrastructure.
System Security¶
OS Hardening¶
We apply this policy to ensure our servers stay safe anytime:
- malicious IP detection and blocking to prevent brute-force
- management interface password access disabled
- management interface root access disabled
- management interface login gracetime
- management interface auto-logout on inactivity
- IPv6 disabled
We enforce standard SSL transport by authorizing only strong cipher suites. You can audit this by checking our SSL-Labs test results.
Rights Management¶
Our containerized infrastructure prevents any malicious propagation if a container is compromised.
Containers communicate on a private network and can’t gain access to resources from other containers except from explicitly defined ones on selected ports.
Furthermore, all files uploaded by users are never stored in a file system (but in a database), preventing malicious files to be executed remotely.
Accounts Management¶
Secrets and credentials like:
- database accounts
- API secrets (JWT signature)
are unique for each of our clients, and strong enough not to be brute-forced (complexity and length).
We deactivate the use of system passwords on management interfaces. Nevertheless, we make sure they’re never stored in plain text on file systems.
SSH access is only available for Toucan Toco’s administrators and managed through a bastion host.
We use certificates to authenticate users and servers. Our bastion service acts as a Certificate Authority and issues these certificates to provides access to servers.
Admin privileges are automatically managed by our Ansible playbooks. The management is a fully automated process with no manual actions arried out by Toucan Toco’s administrators.
Infra Bastion¶
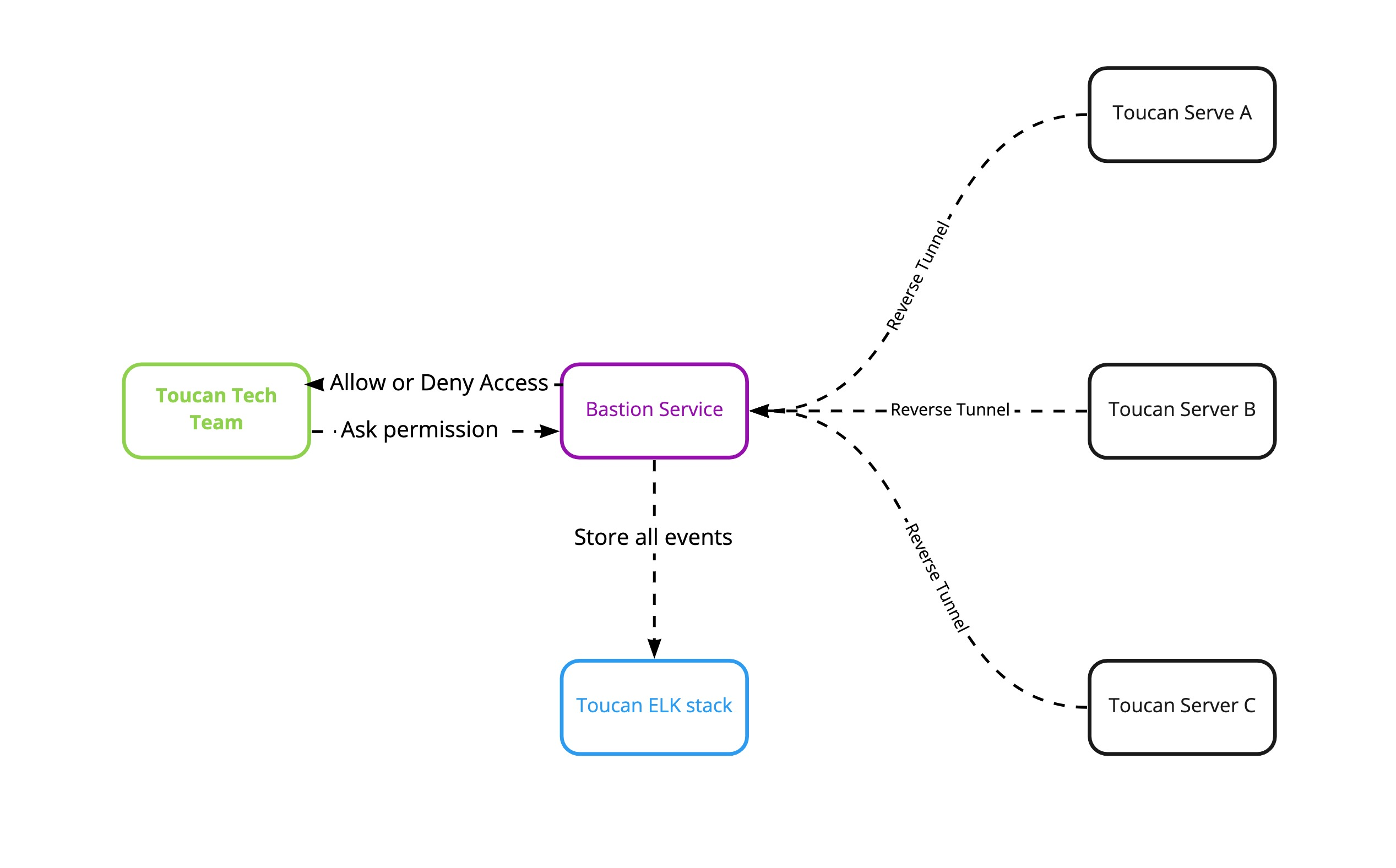
bastion_chart
When a Toucan privileged user needs to access a server in SSH. It requests access from our bastion host . Depending on his user group, his request is accepted or denied.
If his request is accepted, then our bastion host managed SSH access by generating a certificate and an ssh key on the fly at each session. The certificate and the SSH key are used only during the session and deleted then.
Toucan servers are linked through a reverse tunnel and establish a permanent connection to the bastion host. Our bastion is the only service exposed to the world.
We store all logs related to our bastion (session recordings, connections, authentication, nodes) in our ELK stack for audit purposes.
Partition Encryption¶
System or data partitions are not encrypted. But as explained earlier in this document, even in a case of mutual instances, everything is containerized and isolated by design thanks to Docker.
Moreover, keys, application and database passwords are dedicated and different for each instance/project.
Multiple Environments¶
We operate separated staging, preprod and production environments, that are exactly the same with the same backup and monitoring policy.
We considered our demo as if we were one of our own customers! Testing and auditing it will give you the same results as if it was your own instance.
LoadBalancer and Failover¶
Currently the whole frontend stack is fully redundant with a round robin loadbalancer system.
We can lose the half of our frontend stack without any disruption. The recovery process is fully automated and the convergence time is less than 1 minute.
Disaster Recovery Plan - DRP¶
If our datacenter is the victim of a major and critical issue and we lose all our production servers our service will be degraded during the recovery time.
We currently don’t have a fully automated datacenter fallback process. However we have reserved resources in another Scaleway Datacenter where we can redeploy our full infrastructure and data with our automated scripts (thanks to our Infrastructure as Code policy).
By design the DRP of a production client stack is just a basic migration process (redeploy, backup restoration and potential DNS changes) and each step is fully automated.
We use our migration procedure at least once a month. Our DRP uses the same approach as all of our production and client instances and it’s is fully automated.
If we need to restore our infrastrcture from scratch, we will continue to respect our SLA.
General Data Protection Regulation - GDPR¶
Toucan Toco has already filed a statement with the CNIL (Declaration Number: 2129004 v 0). Legal notices on the use of data collected via the website are also available on the Toucan Toco website.
The new requirements of the GDPR are paramount and our team is working diligently to adjust the processes in place to comply with these requirements.
This involves:
- continuing to invest in our security infrastructure
- ensuring that the appropriate contractual conditions are in place
Please check our dedicated public note for more details and informations.
Service Level Agreement - SLA¶
Our SLA includes the following points:
- Clients are able to connect to the Toucan Toco application 24/7 all year long, except during maintenance or infrastructure operations. When these operations produce downtimes, they are scheduled out of business hours and the Toucan Toco ops team will warn the clients by email with details about the downtime period.
- Toucan Toco applications have an uptime of 99.9% over a calendar month.
- The whole infrastructure is monitored and backuped 24/7 all year long.